The post ethical hacker course online free more than 15 hours appeared first on Cyber Hyena.
]]>today we will talk about ethical hacker course online and free this course is full course in one video on YouTube by the cyber mentor Learn network penetration testing / ethical hacking in this full tutorial course for beginners.
This course teaches everything you need to know to get started with ethical hacking and penetration testing. You will learn the practical skills necessary to work in the field. Throughout the course, we will develop our own Active Directory lab in Windows, make it vulnerable, hack it, and patch it. We’ll cover the red and blue sides. We’ll also cover some of the boring stuff like report writing :). This course was originally live streamed weekly on Twitch and built from lessons learned in the previous week.
Course created by The Cyber Mentor. Check out his YouTube channel: here
the best in this ethical hacker course is free and simple and easy to learn the cyber mentor give you the information in easy way also you will learn allot of things in this 15 hours course
you can also see our php free course
Certified Ethical Hacker (CEH) is a qualification obtained by demonstrating knowledge of assessing the security of computer systems by looking for weaknesses and vulnerabilities in target systems, using the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system. This knowledge is assessed by answering multiple choice questions regarding various ethical hacking techniques and tools. The code for the CEH exam is 312-50. This certification has now been made a baseline with a progression to the CEH (Practical), launched in March 2018, a test of penetration testing skills in a lab environment where the candidate must demonstrate the ability to apply techniques and use penetration testing tools to compromise various simulated systems within a virtual environment.
The post ethical hacker course online free more than 15 hours appeared first on Cyber Hyena.
]]>The post super ways to protect wordpress website appeared first on Cyber Hyena.
]]>wordpress are famous php script and the most used script in the world here is some ways to protect wordpress website , after you install and run wordpress and end your theme design you need to do more steps to make it more secure we will use some plugins and other ways will be explained in this article
the first thing you need to do is to install ithemes security plugin
iThemes Security (formerly Better WP Security) gives you over 30+ ways to secure and protect your WordPress site. On average, 30,000 new websites are hacked each day. WordPress sites can be an easy target for attacks because of plugin vulnerabilities, weak passwords and obsolete software.
its a pro and free plugin but the free one have so many great features as you can see we will explained all , after you install the plugin go ahead to the setting of the plugin you will have these page
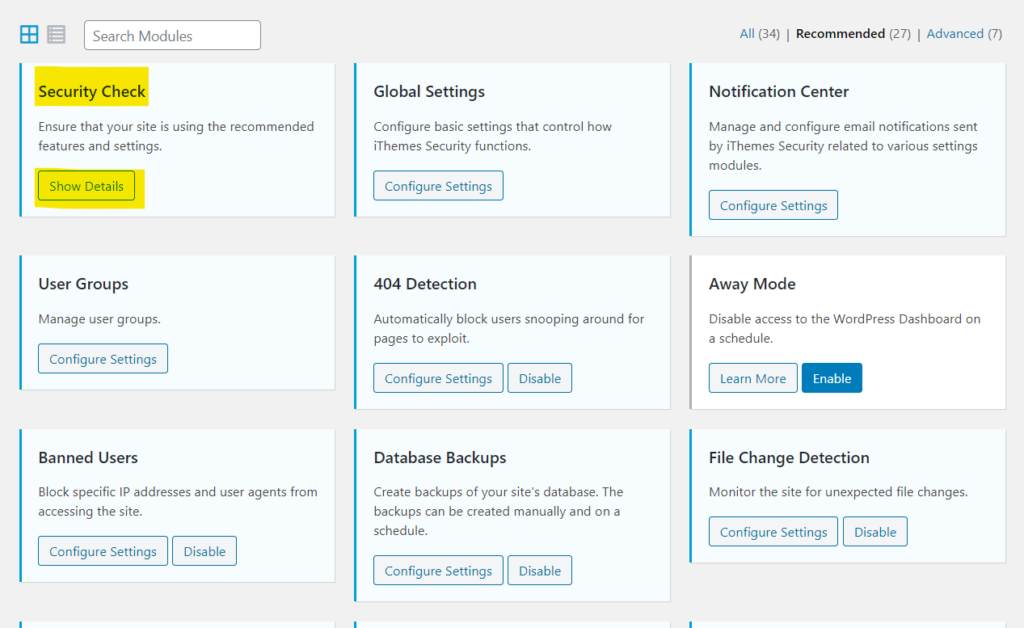
go ahead and run SECURITY CHECK and follow easy steps after the Security Check eanble all the free features which is
404 Detection : if an attacker snooping and searching on your website for pages to exploit , the plugin will ban him
Banned users : you can block speciffic ip adress and users from accessing the website
Database Backups : good option to make secure backups
file Change detection : this feature is important and monitor the site for unexpected file changes which it mostly attackers trying to upload backdoors
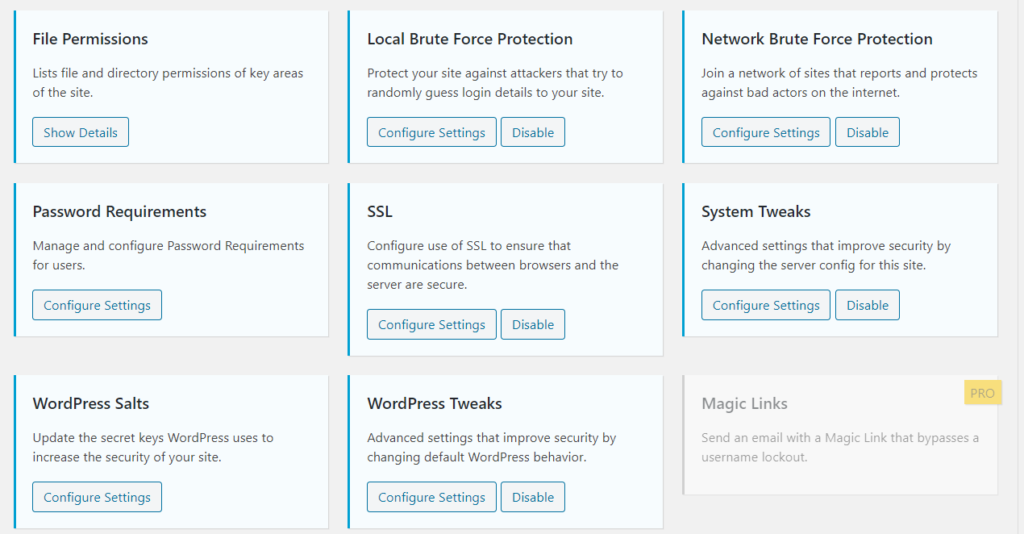
file permissions : good way to give the files and the directories the right permissions
local brute force protection : also a very important feature protect your site against attackers that try to randomly guess login details to your website
ssl and system tweaks and wordpress tweaks : also important features you must enable
in the advanced tab in the settings there is more advanced features
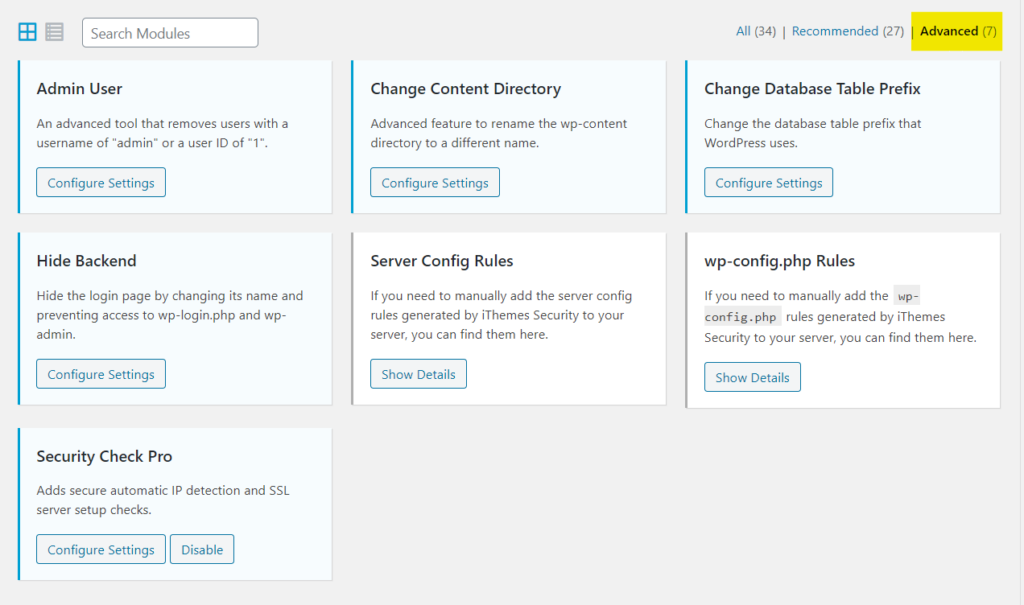
this is so important features but its little advanced and you should be careful and take a back up to your site before you change any thing
the admin user : this will remove the user with iD 1 and username admin from the database to make it more secure and hard to guess
change content directory : its another advanced option to hide wordpress directions like wp-content wp-include its hard to do that , and if you want to do that , do it after your install wordpress if you already designed a theme and you apply it , your theme will be damaged and you should make allot of advanced steps to do it
change database table prefix : usual database prefix is wp for example a user table will be wp_users and that for all wordpress sites , for attacker they know that all wordpress website use the same prefix so this option add random prefix for example wp_users will be EDv_users go ahead and apply it
hide back end : great and important feature you should apply it , its main feautre to protect wordpress site we have full article about it here
server config and wp-config rules : advanced and sensitive to do it by your self if you familiar with server and wp_config.php file you can simple add the codes to the file but be careful
and these is the list of pro features
Pro Features:
- Two-Factor Authentication – Use a mobile app such as Google Authenticator or Authy to generate a code or have a generated code emailed to you.
- WordPress Salts & Security Keys – The iThemes Security plugin makes updating your WordPress keys and salts easy.
- Malware Scan Scheduling – Have your site scanned for malware automatically each day. If an issue is found, an email is sent with the details.
- Password Security – Generate strong passwords right from your profile screen.
- Password Expiration – Set a maximum password age and force users to choose a new password. You can also force all users to choose a new password immediately (if needed).
- Google reCAPTCHA – Protect your site against spammers.
- User Action Logging – Track when users edit content, login or logout.
- Import/Export Settings – Saves time setting up multiple WordPress sites.
- Dashboard Widget – Manage important tasks such as user banning and system scans right from the WordPress dashboard.
- Online File Comparison – When a file change is detected it will scan the origin of the files to determine if the change was malicious or not. Currently works only in WordPress core but plugins and themes are coming.
- Temporary Privilege Escalation – give a contractor or someone else temporary admin or editor access to your site that will automatically reset itself.
- wp-cli Integration – Manage your site’s security from the command line.
important thing if you use theme code editor in wordpress after installing the plugin , that section will disappear because the plugin did that most time attackers use it to edit directly to wordpress code by adding backdoor php code and that will cause the hacking of website , so after you finish your theme editing install the plugin
another thing to do
always update : update are so important for both the wordpress script and the plugins , updates help you to protect wordpress site , updates came with bug fix and exploit fix so its important to update and check updates daily or turn the auto update
we will talk more about advanced security for WordPress
The post super ways to protect wordpress website appeared first on Cyber Hyena.
]]>The post understanding SQL injection test your site and fix solutions appeared first on Cyber Hyena.
]]>SQL injection is a code injection technique that might destroy your database. and its is one of the most common web hacking techniques and it is the placement of malicious code in SQL statements, via web page input.
SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run on your database.
Look at the following example which creates a SELECT statement by adding a variable (txtUserId) to a select string. The variable is fetched from user input (getRequestString):
Example
txtUserId = getRequestString(“UserId”);
txtSQL = “SELECT * FROM Users WHERE UserId = ” + txtUserId;
The rest of this chapter describes the potential dangers of using user input in SQL statements.
SQL Injection Based on 1=1 is Always True
Look at the example above again. The original purpose of the code was to create an SQL statement to select a user, with a given user id.
If there is nothing to prevent a user from entering “wrong” input, the user can enter some “smart” input like this:
UserId:
Then, the SQL statement will look like this:
SELECT * FROM Users WHERE UserId = 105 OR 1=1;
The SQL above is valid and will return ALL rows from the “Users” table, since OR 1=1 is always TRUE.
Does the example above look dangerous? What if the “Users” table contains names and passwords?
The SQL statement above is much the same as this:
SELECT UserId, Name, Password FROM Users WHERE UserId = 105 or 1=1;
A hacker might get access to all the user names and passwords in a database, by simply inserting 105 OR 1=1 into the input field.

lets talk simply , if you not a professional you can know if you have this SQL injection exploit in your website easily using several ways first of all if your site have id’s in the link ,for example if you have like this url in your website www.yoursite.com/news.php?id=1 you can do a quick test just add this Apostrophe ‘ to be like this www.yoursite.com/news.php?id=1’
if you have SQL injection exploit errors will show up or some elements of the website will disappear , IMPORTANT you should know that is just a quick test if you see no errors and nothing disappear that doesn’t mean that you don’t have the exploits to make sure there is another pro way
SQLMAP way
sqlmap is tool programmed using python and easy to use by amateurs you can download the script from the official SQLmap website
you should test your site on localhost not on your server to avoid getting banned by the host provider
after you check if you have a SQL injection exploit in your site how to fix it ?
SQL injection protection: conclusion
Prevention techniques such as input validation, parametrized queries, stored procedures and escaping work well with varying attack vectors. However, because of the large variation in the pattern of SQL injection attacks they are often unable to protect databases.
Therefore, if you want to cover all bases, you should apply the abovementioned strategies in combination with a trusted WAF. The primary WAF benefit is that it provides protection for custom web applications that would otherwise go unprotected.
WAF technology:
- without having to change the application itself.
If you need more detailed control, higher security and lower latency, then the Positive Technologies WAF can help.
- PT WAF does not interfere with the performance of your virtual infrastructure.
- We offer innovative solutions to mitigating SQL injections, XSS, DDoS, zero-day attacks (to name a few) and the threat triaging is done in an automated manner.
- There are multiple deployment options, including cloud, hardware or virtual appliance.
- Our WAF solution also helps you cost-effectively satisfy PCI requirements.
When it comes to configuring, PT WAF takes the time to get to the heart of what matters – because it’s our mission to ensure that our clients’ businesses are never interrupted.
As a leading provider of security solutions, we are committed to continuous improvement, research and practical penetration testing. Test your website today with PT BlackBox Scanner: it’s simple, accurate and free.
also you need to fix it in programming way because some WAF are able to bypass !!
if you don’t have that much Experience you can ask any security professional for further help
The post understanding SQL injection test your site and fix solutions appeared first on Cyber Hyena.
]]>